1 环境介绍
| 系统 | 主机名 | 配置 | 公网IP | 内网IP | VPN内网IP | 硬盘 |
|---|---|---|---|---|---|---|
| Rocky Linux 9.4 | k8s-node2 | 4核4G | 110.40.154.116 | 10.0.0.9 | 10.8.0.16 | 40GB |
2 Harbor介绍
Harbor 是一个开源的注册中心,它通过策略和基于角色的访问控制来保护工件,确保镜像经过扫描且无漏洞,并对镜像进行签名以表明其可信度。Harbor 是一个 CNCF 毕业项目,提供了合规性、性能和互操作性,帮助在 Kubernetes 和 Docker 等云原生计算平台上始终如一且安全地管理工件。
在现代软件开发中,容器化应用已经成为主流,而容器镜像仓库则是确保容器镜像安全、管理和分发的重要工具。Harbor 作为一款开源的企业级容器镜像仓库管理工具,不仅支持多种认证方式,还提供镜像复制、漏洞扫描和用户访问控制等功能,为企业提供了一个安全、高效的镜像管理方案。
本文将详细介绍如何搭建Harbor,并演示如何使用Harbor进行镜像的推送、拉取和管理操作。
3 创建自签发SSL
创建一个自签名的根证书,用于后续签发服务器证书。
有效期设置为 10 年(3650 天),适合长期使用。
3.1 生成根证书颁发机构(CA)
有的人直接就生成服务器证书,这是不对的,需要先生成根证书颁发机构,然后用这个CA去签名证书,以后可以让客户端信任这个CA,所有用这个CA生产的证书都会自动信任。
这条命令生成一个 4096 位的 RSA 私钥,并将其存储在 /usr/local/harbor/certs/ca.key 文件中。私钥是用于签署证书的核心部分。
[root@k8s-node2 ~]# mkdir -p /usr/local/harbor/certs
[root@k8s-node2 ~]# cd /usr/local/harbor/certs
# 创建私钥
openssl genrsa -out /usr/local/harbor/certs/ca.key 4096
[root@k8s-node2 certs]# openssl genrsa -out ca.key 4096 下面这条命令生成一个自签名证书,并将其存储在 /usr/local/harbor/certs/ca.crt文件中。以下是各参数的解释:
# 自签名机构生成CA证书
openssl req -x509 -new -nodes -sha512 -days 3650 -subj "/C=CN/ST=SiChuan/L=Chengdu/O=Company/OU=CD/CN=cncf.net" -key /usr/local/harbor/certs/ca.key -out /usr/local/harbor/certs/ca.crt
[root@k8s-node2 certs]# openssl req -x509 -new -nodes -sha512 -days 3650 -subj "/C=CN/ST=SiChuan/L=Chengdu/O=Company/OU=CD/CN=cncf.net" -key ca.key -out ca.crt参数说明:
-x509:生成一个自签名证书,而不是证书请求(CSR)。
-new:生成一个新的证书。
-nodes:不加密私钥文件。
-sha512:使用 SHA-512 哈希算法。
-days 3650:证书有效期为 3650 天(约 10 年)。
-subj “/C=CN/ST=SiChuan/L=Chengdu/O=Company/OU=CD/CN=cncf.net”,指定证书的主题信息:
国家(C)、州/省(ST)、城市(L)、组织(O)、组织单位(OU)和通用名称(CN)。
-key /usr/local/harbor/certs/ca.key:使用之前生成的私钥。
-out /usr/local/harbor/certs/ca.crt:指定输出的证书文件路径。
用openssl命令查询证书文件,也可以复制到Windows上,直接双击也可以看。
[root@k8s-node2 ~]# openssl x509 -in /usr/local/harbor/certs/ca.crt -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
0a:6c:d7:b3:31:d0:d1:17:92:f2:13:f7:c1:f0:25:0d:2e:0d:ff:c8
Signature Algorithm: sha512WithRSAEncryption
Issuer: C=CN, ST=SiChuan, L=Chengdu, O=Company, OU=CD, CN=cncf.net
Validity
Not Before: Nov 14 05:58:09 2025 GMT
Not After : Nov 12 05:58:09 2035 GMT
Subject: C=CN, ST=SiChuan, L=Chengdu, O=Company, OU=CD, CN=cncf.net
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (4096 bit)
Modulus:
......
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
DA:52:6B:F1:D5:12:3F:2B:07:2C:5E:E7:2E:8A:05:15:B2:51:47:CB
X509v3 Authority Key Identifier:
DA:52:6B:F1:D5:12:3F:2B:07:2C:5E:E7:2E:8A:05:15:B2:51:47:CB
X509v3 Basic Constraints: critical
CA:TRUE
Signature Algorithm: sha512WithRSAEncryption
Signature Value:
......运行以下命令更新 CA 信任存储库,使系统信任新的根证书:
1.Ubuntu系统
update-ca-certificates
2.RHEL/CentOS 7及更高版本)
update-ca-trust3.2 生成服务器私钥及证书请求文件
为 Harbor 仓库生成专属私钥和证书请求文件。
CN=cncf.net 是证书绑定的域名,后续 Harbor 将使用该域名访问。
3.2.1 生成服务器私钥文件
# 服务器私钥文件生成
openssl genrsa -out /usr/local/harbor/certs/cncf.net.key 4096
[root@k8s-node2 certs]# openssl genrsa -out cncf.net.key 40963.2.2 生成证书请求文件
openssl req -sha512 -new -subj "/C=CN/ST=SiChuan/L=Chengdu/O=Company/OU=CD/CN=cncf.net" -key /usr/local/harbor/certs/cncf.net.key -out /usr/local/harbor/certs/cncf.net.csr
# 客户端私钥证书生成
[root@k8s-node2 certs]# openssl req -sha512 -new -subj "/C=CN/ST=SiChuan/L=Chengdu/O=Company/OU=CD/CN=cncf.net" -key cncf.net.key -out cncf.net.csr参数说明:
openssl req -sha512 -new:使用 SHA-512 哈希算法生成一个新的 CSR。
-subj “/C=CN/ST=SiChuan/L=Chengdu/O=Company/OU=CD/CN=cncf.net”:指定 CSR 的主题信息:
/C=CN:国家代码,CN 表示中国。
/ST=SiChuan:州/省,SiChuan 表示四川。
/L=Chengdu:城市,Chengdu 表示成都。
/O=Company:组织名称,Company 表示公司。
/OU=CD:组织单位,CD 表示成都分部。
/CN=cncf.net:通用名称,表示证书的域名。
-key /usr/local/harbor/certs/cncf.net.key:使用之前生成的私钥,存储在 /usr/local/harbor/certs/cncf.net.key 文件中。
-out /usr/local/harbor/certs/cncf.net.csr:指定输出的 CSR 文件路径为 /usr/local/harbor/certs/cncf.net.csr。
3.3 多个域名请求
定义证书扩展信息,包括使用场景、密钥用途和域名绑定。
为刚才的证书颁发请求扩充请求内容,额外增加cncf.com等多个验证域名
subjectAltName 中的 DNS.1、DNS.2、DNS.3、DNS.4是 Harbor 的访问域名。
# 生成多个域名请求
cat > harbor.ext <<-EOF
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
DNS.1=mirrors.harbor.com
DNS.2=mirrors.harbor.cn
DNS.3=mirrors.harbor.net
DNS.4=mirrors.harbor.local
EOF3.4 签发证书
使用自签名根证书为 Harbor 签发正式证书
证书有效期同样为 10 年
用创建的CA机构为证书颁发请求做最终的证书颁发
#使用自签名CA签发证书
openssl x509 -req -sha512 -days 3650 -extfile harbor.ext -CA /usr/local/harbor/certs/ca.crt -CAkey /usr/local/harbor/certs/ca.key -CAcreateserial -in /usr/local/harbor/certs/cncf.net.csr -out /usr/local/harbor/certs/cncf.net.crt
[root@k8s-node2 certs]# openssl x509 -req -sha512 -days 3650 -extfile harbor.ext -CA ca.crt -CAkey ca.key -CAcreateserial -in cncf.net.csr -out cncf.net.crt
Certificate request self-signature ok
subject=C=CN, ST=SiChuan, L=Chengdu, O=Company, OU=CD, CN=cncf.net3.5 信任根证书
由于CA机构是自建的,所以在所有使用此CA颁发的证书位置,都需要信任此CA,才能自动信任由它颁发的证书
1.Ubuntu系统
update-ca-certificates
2.RHEL/CentOS 7及更高版本)
update-ca-trust4 部署Harbor仓库
4.1 部署Docker CE
4.1.1 卸载旧版本
在安装 Docker Engine 之前,需要卸载任何冲突的软件包。
Linux 发行版可能会提供非官方的 Docker 包,这可能会发生冲突 使用 Docker 提供的官方软件包。必须卸载这些包在安装正式版 Docker Engine 之前。
# dnf可能会报告您没有安装这些软件包。
# 存储在 卸载 Docker 时自动删除。/var/lib/docker/
sudo dnf remove docker \
docker-client \
docker-client-latest \
docker-common \
docker-latest \
docker-latest-logrotate \
docker-logrotate \
docker-engine \
podman \
runc4.1.2 使用 rpm 存储库安装
可以根据需要以不同的方式安装 Docker Engine:
可以设置 Docker 的存储库并安装,从他们那里方便安装和升级任务。这是推荐的方法。
可以下载 RPM 包,手动安装,然后管理完全手动升级。适合在无法访问互联网的的系统上安装Docker。
在测试和开发环境中,可以使用自动化便利脚本来安装 Docker。
1.设置存储库
在首次在新主机上安装 Docker Engine 之前,需要设置 Docker 存储库。之后可以从存储库安装和更新 Docker 。
# yum install -y yum-utils device-mapper-persistent-data lvm2
# yum-config-manager --add-repo https://download.docker.com/linux/rhel/docker-ce.repo
sudo dnf -y install dnf-plugins-core
sudo dnf config-manager --add-repo https://download.docker.com/linux/rhel/docker-ce.repo2.安装 Docker 引擎
1.安装 Docker 包
# yum install -y docker-ce docker-ce-cli containerd.io
sudo dnf install docker-ce docker-ce-cli containerd.io docker-buildx-plugin docker-compose-plugin
2.启动 Docker 引擎
sudo systemctl enable --now docker3.关于Docker的完整安装
1.卸载docker旧版本
yum remove docker docker-client docker-client-latest docker-common docker-latest docker-latest-logrotate docker-logrotate docker-selinux docker-engine-selinux docker-engine
2.安装相关工具类
yum install -y yum-utils device-mapper-persistent-data lvm2
3.配置docker仓库(阿里云)
yum-config-manager --add-repo http://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo
4.安装docker
yum install docker-ce
5.验证docker安装成功
#启动docker
systemctl start docker
# 创建开机自启
sudo systemctl enable --now docker
#检查 Docker 服务状态
sudo systemctl status docker
#验证docker
docker run hello-world4.2 Docker 镜像加速器
添加Docker 镜像加速器,这里只限在国内部署时才需要加速,在国外这样加速反而缓慢
sudo mkdir -p /etc/docker
sudo tee /etc/docker/daemon.json <<-'EOF'
{
"registry-mirrors": [
"https://docker.mirrors.ustc.edu.cn",
"https://mirror.baidubce.com",
"https://docker.m.daocloud.io",
"https://mirror.ccs.tencentyun.com",
"https://docker.nju.edu.cn",
"https://docker.mirrors.sjtug.sjtu.edu.cn",
"https://mirror.gcr.io",
"https://docker.registry.cyou",
"https://docker-cf.registry.cyou",
"https://dockercf.jsdelivr.fyi",
"https://docker.jsdelivr.fyi",
"https://dockertest.jsdelivr.fyi",
"https://mirror.aliyuncs.com",
"https://dockerproxy.com"
],
"exec-opts": ["native.cgroupdriver=systemd"]
}
EOF
systemctl daemon-reload
systemctl restart docker4.3 添加Compose支持
下载并安装 Docker Compose 二进制文件,重载 systemd 并重启 Docker 服务,确保配置生效。
curl -L "https://github.com/docker/compose/releases/download/v2.40.3/docker-compose-linux-x86_64" -o /usr/local/bin/docker-compose
# 对二进制文件赋可执行权限
chmod +x /usr/local/bin/docker-compose
sudo systemctl daemon-reload
sudo systemctl restart docker
# 测试docker-compose是否安装成功
[root@k8s-node2 ~]# docker-compose version
Docker Compose version v2.40.34.4 下载并安装Harbor
下载 Harbor 离线安装包,解压到指定目录,并加载 Harbor 所需的镜像。
wget https://github.com/goharbor/harbor/releases/download/v2.14.0/harbor-offline-installer-v2.14.0.tgz
tar xf harbor-offline-installer-v2.14.0.tgz -C /usr/local/bin
cd /usr/local/bin/harbor
# 将名为harbor.v2.14.0.tar.gz的Docker镜像归档文件加载到本地镜像库
[root@k8s-node2 harbor]# docker load -i harbor.v2.14.0.tar.gz
Loaded image: goharbor/harbor-db:v2.14.0
Loaded image: goharbor/harbor-log:v2.14.0
Loaded image: goharbor/trivy-adapter-photon:v2.14.0
Loaded image: goharbor/redis-photon:v2.14.0
Loaded image: goharbor/nginx-photon:v2.14.0
Loaded image: goharbor/registry-photon:v2.14.0
Loaded image: goharbor/prepare:v2.14.0
Loaded image: goharbor/harbor-portal:v2.14.0
Loaded image: goharbor/harbor-core:v2.14.0
Loaded image: goharbor/harbor-jobservice:v2.14.0
Loaded image: goharbor/harbor-registryctl:v2.14.0
Loaded image: goharbor/harbor-exporter:v2.14.0在harbor.yml中,修改以下参数,定义了网址、证书、密码:
设置 Harbor 的访问域名为 mirrors.harbor.com。
指定 HTTPS 使用的证书和私钥路径。
设置管理员密码为 admin。
[root@k8s-node2 harbor]# ll
total 656312
-rw-r--r-- 1 root root 3646 Sep 9 19:44 common.sh
-rw-r--r-- 1 root root 672014938 Sep 9 19:44 harbor.v2.14.0.tar.gz
-rw-r--r-- 1 root root 14688 Sep 9 19:44 harbor.yml.tmpl
-rwxr-xr-x 1 root root 1975 Sep 9 19:44 install.sh
-rw-r--r-- 1 root root 11347 Sep 9 19:44 LICENSE
-rwxr-xr-x 1 root root 2211 Sep 9 19:44 prepare
[root@k8s-node2 harbor]# mv harbor.yml.tmpl harbor.yml
[root@k8s-node2 harbor]# vim harbor.yml
1.修改hostname为mirrors.harbor.com
2.修改https处的certificate为/usr/local/harbor/certs/cncf.net.crt
3.修改https处的private_key为/usr/local/harbor/certs/cncf.net.key
4.修改harbor_admin_password为admin
5.修改https访问时端口号为446
6.修改 data_volume: /data/harbor_dataprepare 会检查配置并生成必要的文件。
install.sh 执行 Harbor 的安装过程,启动所有服务组件。
./prepare
./install.sh
[root@k8s-node2 harbor]# ./install.sh
......
[Step 5]: starting Harbor ...
[+] Running 10/10
✔ Network harbor_harbor Created 0.1s
✔ Container harbor-log Started 0.3s
✔ Container registry Started 0.8s
✔ Container harbor-db Started 0.7s
✔ Container harbor-portal Started 0.9s
✔ Container redis Started 0.9s
✔ Container registryctl Started 0.6s
✔ Container harbor-core Started 1.1s
✔ Container harbor-jobservice Started 1.6s
✔ Container nginx Started 1.6s
✔ ----Harbor has been installed and started successfully.----4.5 生成服务文件
cat > /etc/systemd/system/harbor.service <<EOF
[Unit]
Description=Harbor
After=docker.service systemd-networkd.service systemd-resolved.service
Requires=docker.service
Documentation=http://github.com/vmware/harbor
[Service]
Type=simple
Restart=on-failure
RestartSec=5
ExecStart=/usr/local/bin/docker-compose -f /usr/local/bin/harbor/docker-compose.yml up
ExecStop=/usr/local/bin/docker-compose -f /usr/local/bin/harbor/docker-compose.yml down
[Install]
WantedBy=multi-user.target
EOF
sudo systemctl daemon-reload
systemctl enable harbor --now
# harbor修改配置文件后重启
[root@k8s-node2 ~]# cd /usr/local/bin/harbor/
[root@k8s-node2 harbor]# ll
total 656324
drwxr-xr-x 3 root root 4096 Nov 14 16:13 common
-rw-r--r-- 1 root root 3646 Sep 9 19:44 common.sh
-rw-r--r-- 1 root root 6015 Nov 14 16:14 docker-compose.yml
-rw-r--r-- 1 root root 672014938 Sep 9 19:44 harbor.v2.14.0.tar.gz
-rw-r--r-- 1 root root 14724 Nov 14 16:12 harbor.yml
-rwxr-xr-x 1 root root 1975 Sep 9 19:44 install.sh
-rw-r--r-- 1 root root 11347 Sep 9 19:44 LICENSE
-rwxr-xr-x 1 root root 2211 Sep 9 19:44 prepare
# 停止harbor
[root@k8s-node2 harbor]# docker-compose down
# 配置文件检查
[root@k8s-node2 harbor]# ./prepare
# 启动harbor
[root@k8s-node2 harbor]# docker-compose up -d4.6 页面访问测试
地址: https://110.40.154.116:447、https://mirrors.harbor.com:446
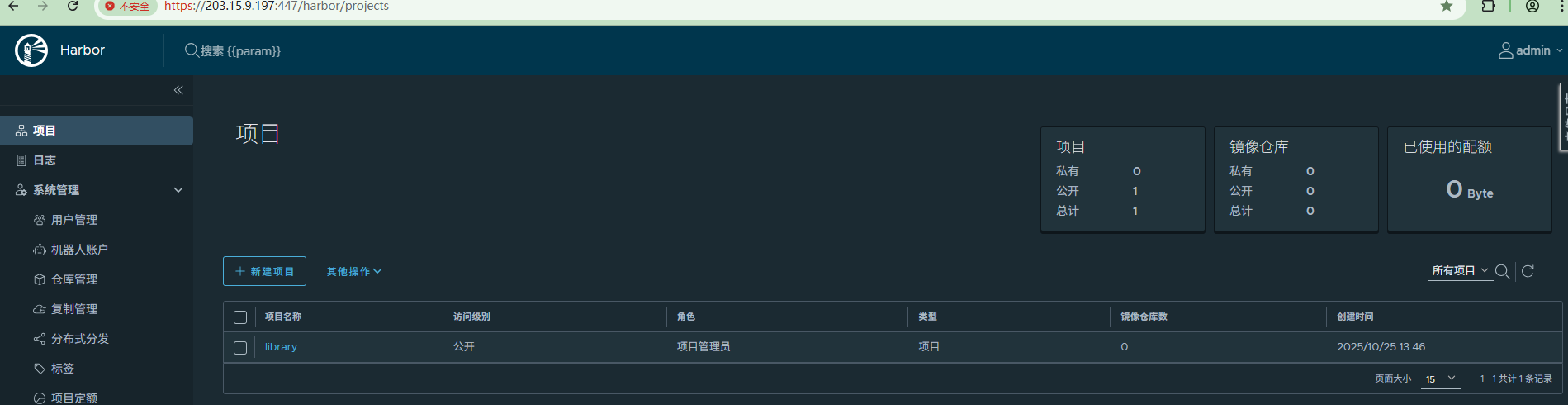
Windows在hosts文件配置域名解析后,可实现域名访问
5 推送镜像到harbor
登录 Harbor 仓库。
使用 tag 命令将本地镜像重命名为符合 Harbor 格式的路径。
使用 push 命令将镜像上传到 Harbor 仓库。
上传前请确保所有机器 /etc/hosts文件中已添加mirrors.harbor.com 的 IP 映射。
[root@k8s-master ~]# cat /etc/hosts
......
10.8.0.13 k8s-master
10.8.0.14 k8s-node1
10.8.0.16 k8s-node2
10.8.0.17 k3s-master
110.40.154.116 mirrors.harbor.com
[root@k8s-node1 ~]# cat /etc/hosts
......
10.8.0.13 k8s-master
10.8.0.14 k8s-node1
10.8.0.16 k8s-node2
10.8.0.17 k3s-master
110.40.154.116 mirrors.harbor.com
[root@k8s-node2 ~]# cat /etc/hosts
......
10.8.0.13 k8s-master
10.8.0.14 k8s-node1
10.8.0.16 k8s-node2
10.8.0.17 k3s-master
110.40.154.116 mirrors.harbor.com
[root@k3s-master ~]# vim /etc/hosts
......
10.8.0.13 k8s-master
10.8.0.14 k8s-node1
10.8.0.16 k8s-node2
10.8.0.17 k3s-master
110.40.154.116 mirrors.harbor.com5.1 Containerd容器
5.1.1 配置harbor证书
1.配置k8s-master、k8s-node1、k8s-node2、k3s-master
# 创建证书目录
sudo mkdir -p /etc/containerd/certs.d/mirrors.harbor.com:446
# 将Harbor的CA证书复制到上述目录
[root@k8s-node2 ~]# scp /usr/local/harbor/certs/ca.crt root@49.235.53.189:/etc/containerd/certs.d/mirrors.harbor.com:446
[root@k8s-node2 ~]# scp /usr/local/harbor/certs/ca.crt root@150.158.57.109:/etc/containerd/certs.d/mirrors.harbor.com:446
[root@k8s-node2 ~]# scp /usr/local/harbor/certs/ca.crt /etc/containerd/certs.d/mirrors.harbor.com:446
[root@k8s-node2 ~]# scp /usr/local/harbor/certs/ca.crt root@124.222.84.111:/etc/containerd/certs.d/mirrors.harbor.com:446
[root@k8s-master ~]# cd /etc/containerd/certs.d/mirrors.harbor.com:446
[root@k8s-master mirrors.harbor.com:446]# ll
total 0
[root@k8s-master mirrors.harbor.com:446]# ll
total 4
-rw-r--r-- 1 root root 2021 Nov 16 14:37 ca.crt
[root@k8s-node1 ~]# sudo mkdir -p /etc/containerd/certs.d/mirrors.harbor.com:446
[root@k8s-node1 ~]# cd /etc/containerd/certs.d/mirrors.harbor.com:446
[root@k8s-node1 mirrors.harbor.com:446]# ll
total 4
-rw-r--r-- 1 root root 2021 Nov 16 14:46 ca.crt
[root@k8s-node2 ~]# cd /etc/containerd/certs.d/mirrors.harbor.com:446
[root@k8s-node2 mirrors.harbor.com:446]# ll
total 4
-rw-r--r-- 1 root root 2021 Nov 16 14:50 ca.crt
[root@k3s-master ~]# cd /etc/containerd/certs.d/mirrors.harbor.com:446
[root@k3s-master mirrors.harbor.com:446]# ll
total 4
-rw-r--r-- 1 root root 2021 Nov 17 16:37 ca.crt
# 复制证书到系统信任目录
[root@k8s-node2 ~]# scp /usr/local/harbor/certs/ca.crt root@49.235.53.189:/etc/pki/ca-trust/source/anchors/
[root@k8s-node2 ~]# scp /usr/local/harbor/certs/ca.crt root@150.158.57.109:/etc/pki/ca-trust/source/anchors/
[root@k8s-node2 ~]# scp /usr/local/harbor/certs/ca.crt /etc/pki/ca-trust/source/anchors/
[root@k8s-node2 ~]# scp /usr/local/harbor/certs/ca.crt root@124.222.84.111:/etc/pki/ca-trust/source/anchors/
[root@k8s-master ~]# cd /etc/pki/ca-trust/source/anchors/
[root@k8s-master anchors]# ll
total 4
-rw-r--r-- 1 root root 2021 Nov 16 14:40 ca.crt
[root@k8s-node1 ~]# cd /etc/pki/ca-trust/source/anchors/
[root@k8s-node1 anchors]# ll
total 4
-rw-r--r-- 1 root root 2021 Nov 16 14:47 ca.crt
[root@k8s-node2 ~]# cd /etc/pki/ca-trust/source/anchors/
[root@k8s-node2 anchors]# ll
total 4
-rw-r--r-- 1 root root 2021 Nov 16 14:51 ca.crt
[root@k3s-master ~]# cd /etc/pki/ca-trust/source/anchors/
[root@k3s-master anchors]# ll
total 4
-rw-r--r-- 1 root root 2021 Nov 17 16:39 ca.crt
# 信任证书
update-ca-trust
# 重启containerd服务
systemctl restart containerd.service5.1.2 登录harbor
[root@k8s-master ~]# nerdctl login mirrors.harbor.com:446 -u admin -p admin
WARN[0000] WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARNING! Your credentials are stored unencrypted in '/root/.docker/config.json'.
Configure a credential helper to remove this warning. See
https://docs.docker.com/go/credential-store/
Login Succeeded
[root@k8s-node1 ~]# nerdctl login mirrors.harbor.com:446 -u admin -p admin
WARN[0000] WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARNING! Your credentials are stored unencrypted in '/root/.docker/config.json'.
Configure a credential helper to remove this warning. See
https://docs.docker.com/go/credential-store/
Login Succeeded
[root@k8s-node2 ~]# nerdctl login mirrors.harbor.com:446 -u admin -p admin
WARN[0000] WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARNING! Your credentials are stored unencrypted in '/root/.docker/config.json'.
Configure a credential helper to remove this warning. See
https://docs.docker.com/go/credential-store/
Login Succeeded
[root@k3s-master ~]# nerdctl login mirrors.harbor.com:446 -u admin -p admin
WARN[0000] WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARNING! Your credentials are stored unencrypted in '/root/.docker/config.json'.
Configure a credential helper to remove this warning. See
https://docs.docker.com/go/credential-store/
Login Succeeded5.1.3 标记与推送镜像
[root@k8s-master ~]# nerdctl tag calico/whisker-backend:v3.30.4 mirrors.harbor.com:446/calico_image/calico/whisker-backend:v3.30.4
[root@k8s-master ~]# nerdctl images
REPOSITORY TAG IMAGE ID CREATED PLATFORM SIZE BLOB SIZE
mirrors.harbor.com:446/calico_image/calico/whisker-backend v3.30.4 e67ef5e60f91 About a minute ago linux/amd64 75.49MB 33.08MB
calico/whisker-backend v3.30.4 e67ef5e60f91 3 days ago linux/amd64 75.49MB 33.08MB
[root@k8s-master ~]# nerdctl push mirrors.harbor.com:446/calico_image/calico/whisker-backend:v3.30.4
INFO[0000] pushing as a reduced-platform image (application/vnd.docker.distribution.manifest.list.v2+json, sha256:ad428c8646c12c0e8a13ed24f0b17ae4909c3f25d1069f66c02ed44fc1468152)
index-sha256:ad428c8646c12c0e8a13ed24f0b17ae4909c3f25d1069f66c02ed44fc1468152: done |++++++++++++++++++++++++++++++++++++++|
manifest-sha256:3662f3d27a0ee9498dac2ef7a5c6f421f6008da651156cc75dfa13a7f21ec739: done |++++++++++++++++++++++++++++++++++++++|
config-sha256:28075ea09dfb6b76cb5a8c5d750213a01dad91895605b685cebafb3badcd1ac8: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:2fb7b31fc26f44f47297f3510ccd3eb4188ba9e9cf6e8fca1591dd811f4c8ef5: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:7617061f80128ccedf4ed90fa70753bca18ad8fed27e6da0c71f90b9db59e24b: done |++++++++++++++++++++++++++++++++++++++|
elapsed: 93.6s total: 31.6 M (345.1 KiB/s)5.1.4 拉取镜像
[root@k8s-master ~]# nerdctl pull mirrors.harbor.com:446/library/calico/node:v1.38.7
mirrors.harbor.com:447/library/calico/node:v1.38.7: resolved |++++++++++++++++++++++++++++++++++++++|
index-sha256:8532d21c0c85ca22e337c3125e84c575d77b6d59faae181e2cdd0adfd3abd1bf: done |++++++++++++++++++++++++++++++++++++++|
manifest-sha256:b6c92e535b935575f48092edadcfaec716ebce53f1fbc56d312744e86ce0fb17: done |++++++++++++++++++++++++++++++++++++++|
config-sha256:833e8e11d9dc187377eab6f31e275114a6b0f8f0afc3bf578a2a00507e85afc9: done |++++++++++++++++++++++++++++++++++++++|
elapsed: 1.2 s total: 0.0 B (0.0 B/s)5.2 Docker容器
5.2.1 配置harbor证书
sudo mkdir -p /etc/docker/certs.d/mirrors.harbor.com:446
# 将Harbor的CA证书复制到该目录
[root@k8s-node2 ~]# scp /usr/local/harbor/certs/ca.crt root@49.235.53.189:/etc/docker/certs.d/mirrors.harbor.com:446
[root@k8s-node2 ~]# scp /usr/local/harbor/certs/ca.crt root@150.158.57.109:/etc/docker/certs.d/mirrors.harbor.com:446
[root@k8s-node2 ~]# scp /usr/local/harbor/certs/ca.crt /etc/docker/certs.d/mirrors.harbor.com:446
[root@k8s-node2 ~]# scp /usr/local/harbor/certs/ca.crt root@124.222.84.111:/etc/docker/certs.d/mirrors.harbor.com:446
[root@k8s-master ~]# cd /etc/docker/certs.d/mirrors.harbor.com:446
[root@k8s-master mirrors.harbor.com:446]# ll
total 4
-rw-r--r-- 1 root root 2021 Nov 16 15:47 ca.crt
[root@k8s-node1 ~]# cd /etc/docker/certs.d/mirrors.harbor.com:446
[root@k8s-node1 mirrors.harbor.com:446]# ll
total 4
-rw-r--r-- 1 root root 2021 Nov 16 15:50 ca.crt
[root@k8s-node2 ~]# cd /etc/docker/certs.d/mirrors.harbor.com:446
[root@k8s-node2 mirrors.harbor.com:446]# ll
total 4
-rw-r--r-- 1 root root 2021 Nov 16 15:52 ca.crt
[root@k3s-master ~]# cd /etc/docker/certs.d/mirrors.harbor.com:446
[root@k3s-master mirrors.harbor.com:446]# ll
total 4
-rw-r--r-- 1 root root 2021 Nov 17 16:46 ca.crt
# 复制证书到系统信任目录
[root@k8s-node2 ~]# scp /usr/local/harbor/certs/ca.crt root@49.235.53.189:/etc/pki/ca-trust/source/anchors/
[root@k8s-node2 ~]# scp /usr/local/harbor/certs/ca.crt root@150.158.57.109:/etc/pki/ca-trust/source/anchors/
[root@k8s-node2 ~]# scp /usr/local/harbor/certs/ca.crt /etc/pki/ca-trust/source/anchors/
[root@k8s-node2 ~]# scp /usr/local/harbor/certs/ca.crt root@124.222.84.111:/etc/pki/ca-trust/source/anchors/
[root@k8s-master ~]# cd /etc/pki/ca-trust/source/anchors/
[root@k8s-master anchors]# ll
total 4
-rw-r--r-- 1 root root 2021 Nov 16 14:40 ca.crt
[root@k8s-node1 ~]# cd /etc/pki/ca-trust/source/anchors/
[root@k8s-node1 anchors]# ll
total 4
-rw-r--r-- 1 root root 2021 Nov 16 14:47 ca.crt
[root@k8s-node2 ~]# cd /etc/pki/ca-trust/source/anchors/
[root@k8s-node2 anchors]# ll
total 4
-rw-r--r-- 1 root root 2021 Nov 16 14:51 ca.crt
[root@k3s-master ~]# cd /etc/pki/ca-trust/source/anchors/
[root@k3s-master anchors]# ll
total 4
-rw-r--r-- 1 root root 2021 Nov 17 16:47 ca.crt
# 信任证书
update-ca-trust
# 重启docker服务
systemctl restart docker5.2.3 登录harbor
[root@k8s-master ~]# docker login mirrors.harbor.com:446 -u admin -p admin
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
Login Succeeded
[root@k8s-node1 ~]# docker login mirrors.harbor.com:446 -u admin -p admin
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
Login Succeeded
[root@k8s-node2 ~]# docker login mirrors.harbor.com:446 -u admin -p admin
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
Login Succeeded
[root@k3s-master ~]# docker login mirrors.harbor.com:446 -u admin -p admin
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
Login Succeeded5.2.4 标记与推送镜像
[root@k8s-master ~]# docker pull mirrors.harbor.com:446/calico_image/calico/node:v3.30.4
v3.30.4: Pulling from calico_image/calico/node
44c2028a3ff8: Pull complete
Digest: sha256:8532d21c0c85ca22e337c3125e84c575d77b6d59faae181e2cdd0adfd3abd1bf
Status: Downloaded newer image for mirrors.harbor.com:446/calico_image/calico/node:v3.30.4
mirrors.harbor.com:446/calico_image/calico/node:v3.30.4
[root@k8s-master ~]# docker images
i Info → U In Use
IMAGE ID DISK USAGE CONTENT SIZE EXTRA
mirrors.harbor.com:446/calico_image/calico/node:v3.30.4 8532d21c0c85 563MB 157MB
1.标记镜像
docker tag SOURCE_IMAGE[:TAG] harbor.cncf.net:446/library/REPOSITORY[:TAG]
[root@k8s-master ~]# docker tag mirrors.harbor.com:446/calico_image/calico/node:v3.30.4 mirrors.harbor.com:446/library/calico/node:v3.30.4
[root@k8s-master ~]# docker images
i Info → U In Use
IMAGE ID DISK USAGE CONTENT SIZE EXTRA
mirrors.harbor.com:446/calico_image/calico/node:v3.30.4 8532d21c0c85 563MB 157MB
mirrors.harbor.com:446/library/calico/node:v3.30.4 8532d21c0c85 563MB 157MB
2.推送镜像到harbor
docker push mirrors.harbor.com:446/library/REPOSITORY[:TAG]
[root@k8s-master ~]# docker push mirrors.harbor.com:446/library/calico/node:v3.30.4
The push refers to repository [mirrors.harbor.com:446/library/calico/node]
44c2028a3ff8: Mounted from calico_image/calico/node
v3.30.4: digest: sha256:8532d21c0c85ca22e337c3125e84c575d77b6d59faae181e2cdd0adfd3abd1bf size: 3175.2.5 拉取镜像
[root@k8s-master ~]# docker pull mirrors.harbor.com:446/calico_image/calico/cni:v3.30.4